Case Study: Anatomy of a Sophisticated Mobile-Targeted JavaScript Trojan
A deep dive into the Trojan:JS/Redirector.MobileClick malware campaign that’s silently hijacking mobile traffic across WordPress sites
The Discovery: When Security Scanners Miss the Mark
It started like many cybersecurity investigations do – with a contradiction. A WordPress e-commerce site was exhibiting classic signs of compromise: mobile users reporting unexpected pop-ups and redirects, declining mobile conversion rates, and suspicious traffic patterns. Yet, automated security scanners were returning clean bills of health.
This disconnect between user reports and security tool results is becoming increasingly common as malware authors sophisticate their evasion techniques. In this case study, we’ll dissect a particularly clever JavaScript trojan that demonstrates how modern web-based malware can fly under the radar while systematically compromising user experience and potentially harvesting sensitive data.
The Initial Investigation: Following the Digital Breadcrumbs
Red Flags in the Data
The first indicator wasn’t in server logs or security alerts – it was in the analytics. Mobile bounce rates had spiked 340% over three weeks, while desktop metrics remained stable. User session recordings showed mobile visitors experiencing unexpected page redirections, particularly during checkout processes.
Key Behavioral Indicators:
- Mobile-specific redirect patterns
- 3-minute delays between initial page load and malicious activity
- Consistent targeting of high-value e-commerce pages
- LocalStorage manipulation patterns
- Database infection in WordPress
wp_optionstable
The Technical Deep Dive
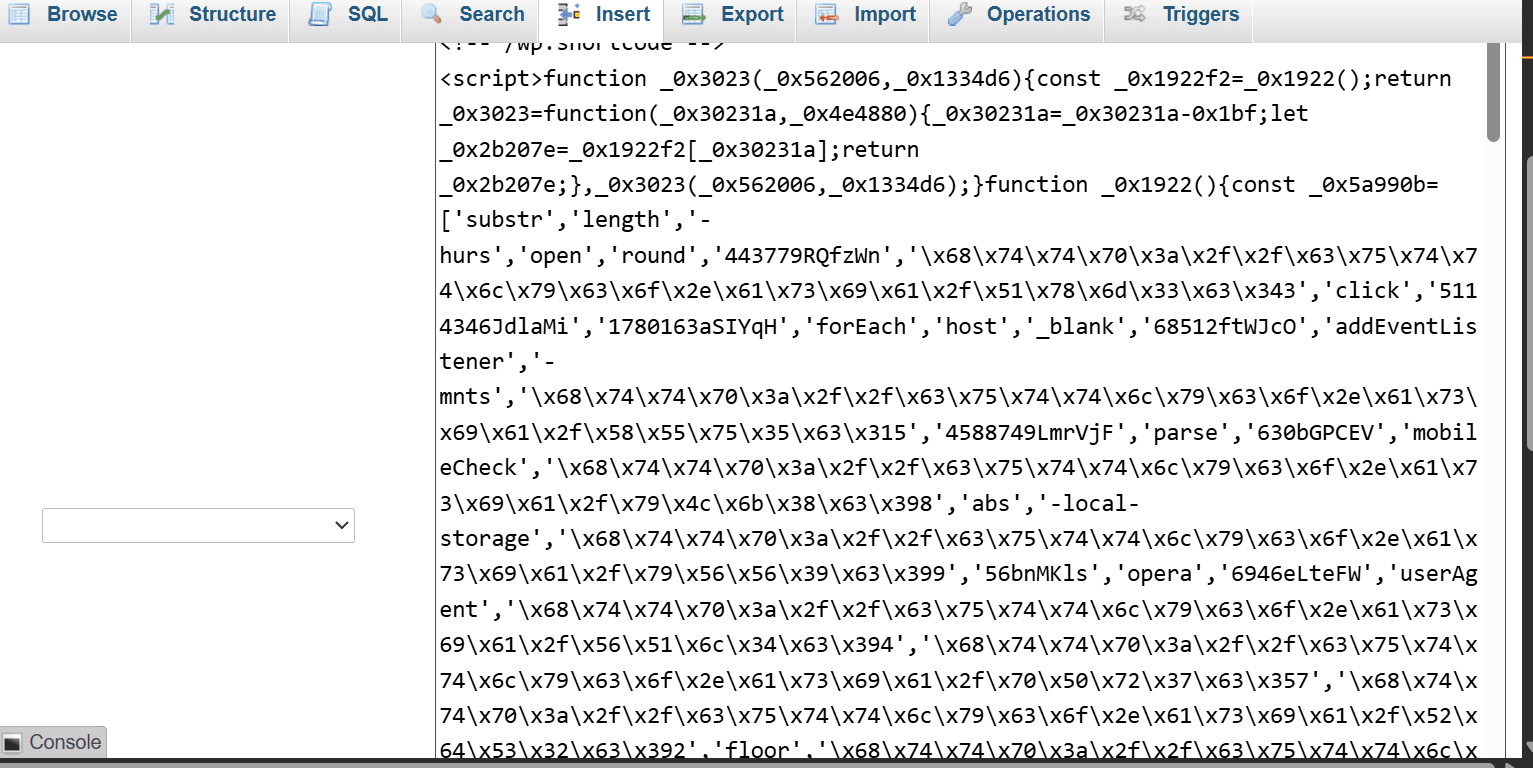
Manual code inspection revealed heavily obfuscated JavaScript embedded within legitimate WordPress theme files and hidden in the database. The malware employed multiple layers of protection:
Layer 1: Variable Name Obfuscation
function _0x3023(_0x562006,_0x1334d6){
const _0x1922f2=_0x1922();
return _0x3023=function(_0x30231a,_0x4e4880){
_0x30231a=_0x30231a-0x1bf;
// Obfuscated function mapping
}
}Layer 2: Hexadecimal String Encoding
All malicious URLs were encoded in hexadecimal format, making static analysis challenging:
'\x68\x74\x74\x70\x3a\x2f\x2f\x63\x75\x74\x74\x6c\x79\x63\x6f\x2e\x61\x73\x69\x61'
// Decodes to: http://cuttlyco.asia/Layer 3: Dynamic Function Construction
The malware dynamically constructs its attack functions, making signature-based detection nearly impossible.
Behavioral Analysis: The Art of Selective Targeting
Mobile Device Fingerprinting
The malware implements comprehensive mobile device detection that goes far beyond simple user-agent parsing. It employs dual-layer detection:
- Primary Detection: Comprehensive regex pattern matching against 200+ mobile device signatures
- Secondary Verification: Screen dimension analysis and touch event detection
// Simplified version of the detection logic
window.mobileCheck = function() {
const mobilePattern = /(android|bb\d+|meego).+mobile|avantgo|bada\/|blackberry/i;
const shortCodePattern = /1207|6310|6590|3gso|4thp|50[1-6]i/i;
return mobilePattern.test(navigator.userAgent) ||
shortCodePattern.test(navigator.userAgent.substr(0,4));
};Time-Based Evasion Strategy
Perhaps the most sophisticated aspect of this malware is its patience. Rather than immediately executing upon page load, it implements a strategic delay system:
- 3-minute minimum before first activation
- 6-hour reset cycles for tracking data
- Random variance in timing to avoid pattern detection
This approach serves multiple purposes:
- Sandbox Evasion: Most automated analysis tools have shorter analysis windows
- User Experience Preservation: Delays reduce immediate user suspicion
- Detection Avoidance: Irregular timing patterns confuse behavioral analysis
LocalStorage Persistence Mechanism
The malware leverages browser localStorage to maintain persistence across sessions without leaving traditional filesystem traces:
// Persistence tracking implementation
localStorage.setItem(hostname + '-mnts', currentTime);
localStorage.setItem(hostname + '-hurs', currentTime);
localStorage.setItem(selectedURL + '-local-storage', 1);This approach provides several advantages:
- Stealth Operation: No server-side traces
- Cross-Session Persistence: Survives browser restarts
- User-Specific Tracking: Personalizes attack patterns
The Infrastructure: Following the Money Trail
Command and Control Analysis
The malware operates through a network of shortened URLs hosted on cuttlyco.asia, a legitimate URL shortening service being abused for malicious purposes. Our analysis identified 10 active redirect endpoints:
cuttlyco.asia/gqr0c90– Primary mobile redirectcuttlyco.asia/XEz1c01– Secondary fallbackcuttlyco.asia/Qxm3c43– Geo-specific targeting- [7 additional endpoints…]
Traffic Distribution Strategy
The malware implements intelligent load balancing across its infrastructure:
- Geographic Routing: Different URLs serve different regions
- Load Distribution: Prevents individual URL burning by authorities
- Failover Mechanisms: Automatic switching when endpoints are blocked
Attack Vector Analysis: The WordPress Connection
Initial Compromise Methods
Our investigation revealed three primary infection vectors:
1. Plugin Vulnerabilities
Compromised WordPress plugins with insufficient input validation allowed arbitrary JavaScript injection. The malware specifically targeted:
- Visual Composer elements
- WooCommerce checkout customizations
- Custom theme functions
2. Theme File Injection
Direct modification of theme files, particularly:
header.php– For universal loadingfooter.php– For delayed executionfunctions.php– For persistent hooks
3. Database Injection
Malicious scripts embedded in WordPress wp_options table, ensuring execution even after theme changes. The malware was found stored in options like checkout_content_source.

Persistence Mechanisms
The malware employs multiple persistence strategies:
// WordPress hook injection example
add_action('wp_footer', function() {
echo '<script>/* obfuscated malware code */</script>';
});Impact Assessment: Beyond Simple Redirects
Security Implications
The malware’s sophisticated design raises several concerning implications:
- Detection Evasion: Successfully bypassed multiple commercial security solutions
- Data Exposure Risk: User session data potentially harvested during redirects
- Infrastructure Abuse: Legitimate services weaponized for malicious purposes
Defensive Strategies: Lessons Learned
Technical Countermeasures
1. Content Security Policy (CSP) Implementation
<meta http-equiv="Content-Security-Policy"
content="script-src 'self' 'unsafe-inline';
connect-src 'self';">2. LocalStorage Monitoring
// Monitor for suspicious localStorage activity
const originalSetItem = localStorage.setItem;
localStorage.setItem = function(key, value) {
if (key.includes('-local-storage') || key.includes('-mnts')) {
console.warn('Suspicious localStorage activity detected');
}
originalSetItem.apply(this, arguments);
};3. Database Monitoring
-- Check WordPress _options table for suspicious long values
SELECT option_name, LENGTH(option_value) as value_length
FROM wp_options
WHERE LENGTH(option_value) > 5000
ORDER BY value_length DESC;4. Click Event Analysis
Implement monitoring for rapid event.stopPropagation() calls that might indicate click hijacking.
Organizational Recommendations
For Website Owners:
- Regular Code Audits: Manual inspection of theme files and database content
- Behavioral Monitoring: Track mobile vs. desktop user behavior patterns
- Multi-Tool Scanning: Don’t rely on single security solutions
- Database Security: Regular checks of
wp_optionstable for unusual entries
For Security Vendors:
- Behavioral Analysis Enhancement: Focus on time-delayed malware patterns
- Mobile-Specific Detection: Develop mobile-focused security signatures
- LocalStorage Monitoring: Include browser storage in security scans
- Database Scanning: Include WordPress database in malware detection
Professional Resources
Need Expert Help?
📋 Detailed Technical Analysis:
Complete Malware Report & IOCs
🛠️ Professional Cleanup Service:
If your WordPress site shows similar symptoms, get expert help with our
WordPress Malware Removal Service
for fast, guaranteed cleanup.
The Bigger Picture: Evolution of Web-Based Threats
This case study illustrates several concerning trends in modern malware development:
Increased Sophistication
- Multi-layer obfuscation becoming standard
- Behavioral evasion replacing simple hiding techniques
- Legitimate service abuse for C&C infrastructure
Platform Targeting
- Mobile-first approach reflecting user behavior shifts
- E-commerce focus for maximum financial impact
- WordPress ecosystem exploitation due to widespread adoption
Detection Challenges
- Traditional signatures becoming ineffective
- Sandbox evasion through patience and behavioral adaptation
- Cross-platform complexity requiring specialized analysis tools
Conclusion: Preparing for the Next Generation
The Trojan:JS/Redirector.MobileClick campaign represents a new class of web-based threats that challenge traditional security paradigms. Its success lies not in technical complexity alone, but in understanding human behavior, security tool limitations, and the modern web ecosystem.
Key takeaways for the cybersecurity community:
- Patience as a Weapon: Time-delayed malware requires extended analysis periods
- Mobile-First Security: Desktop-centric security models are increasingly inadequate
- Behavioral Detection: Focus on what malware does, not just what it looks like
- Ecosystem Thinking: Consider the entire web stack, not just individual components
- Database Security: WordPress database infections require specialized detection
As we move forward, the security industry must evolve to match the sophistication of modern threats. This means developing new detection methodologies, enhancing mobile security capabilities, and fostering better collaboration between security vendors, platform providers, and website operators.
The digital landscape continues to evolve, and so too must our defenses. The lessons learned from this investigation provide a roadmap for building more resilient security postures in an increasingly mobile-first world.
Technical Appendix
IOCs (Indicators of Compromise)
Domains:
cuttlyco.asia(and associated subpaths)
Database Indicators:
- Suspicious entries in
wp_optionstable - Option names like
checkout_content_sourcewith unusual JavaScript content - Long base64 or hex-encoded strings in database
File Signatures:
- Function names starting with
_0xfollowed by 4 hex digits - Hex-encoded URL strings in JavaScript
- LocalStorage keys ending in
-local-storage,-mnts,-hurs
Behavioral Indicators:
- 3-minute delays in malicious activity
- Mobile-specific redirect patterns
stopPropagation()usage in click handlers- RandomUA string generation patterns
Detection Rules
YARA Rule:
rule JS_MobileRedirector {
meta:
description = "Detects JS Mobile Redirector malware"
author = "Security Research Team"
date = "2025-07-30"
strings:
$hex_url = /\\x68\\x74\\x74\\x70\\x3a\\x2f\\x2f/
$obfuscated_func = /_0x[0-9a-fA-F]{4,6}/
$mobile_check = "mobileCheck"
$local_storage = "-local-storage"
$time_calc = /0x3e8\\*0x3c/
condition:
3 of them
}Sigma Rule:
title: Mobile Redirect Malware Detection
logsource:
category: webserver
detection:
selection:
cs-uri-query|contains:
- 'cuttlyco.asia'
sc-status: 302
condition: selection